Overview
| Unexpected or out-of-specification behavior in any system presents a security vulnerability. A system’s security is often only as strong as its weakest component, so a single point of incorrect behavior can result in the compromise of an entire system. Led by Professor Yih-Chun Hu and completed in the first quarter of 2012, this investigation focused on potential vulnerabilities in the WiMAX protocol and the implementations thereof. | ||
Motivation and ObjectivesRecently, the software verification community developed a technique called fuzzing that could automate the detection of unusual behavior. In particular, in fuzzing, a system evaluator sends a variety of invalid inputs to the system under test, and observes the behavior of the system. If the system crashes or displays other unusual behaviors, the evaluator uses debugging tools to analyze and reverse engineer the misbehaving source code, especially to determine whether the unusual behaviors represent a feasible path of exploit. Though fuzzing was initially aimed at user-mode programs, they have since been extended to protocol implementations. In this project, we evaluated several WiMAX implementations using fuzzing based on the WiMAX protocol conformance testers and other tools as appropriate (in particular, a software radio). Specifically, this project explored and identified MAC layer design issues in the areas of security and performance through practical testing of existing MAC layer implementations. |
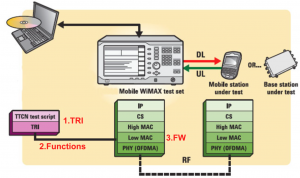 Operation stack of the protocol conformance tester
|
|
ResultsThis project assessed the feasibility and subsequently developed a fuzzing engine, tools, and techniques that enable over-the-air fuzzing. The project scope included investigating the design of the WiMAX MAC protocol and its security mechanisms (with a focus on management and control plane only) and developing a framework and tools that would allow us to conduct fuzzing (over-the-air) on a WiMAX base station implementation. |
||
Synergy and CollaborationsThis research is funded by Singapore’s Centre for Strategic Infocomm Technologies. |
||