|
Smart Grid Stability Under Dynamic Pricing Attack
|
| Computer communication networks and smart meters are essential components of Smart Grids and are subject to security threats. In dynamic pricing systems, these components are used to communicate price and demand response signals between system operators and consumers. In this study, we assess the impact on dynamic pricing systems caused by adversaries who aim to destabilize the system by compromising these signals. This can lead to severe consequences, such as regional blackouts and extended service interruptions. |
 |
Our Approach
We develop a holistic analysis framework by combining the physical model of electricity demand and supply, the communication model for the price signals to be transmitted, and various parameterized attack models. We study the impact of varying attack parameters on the security of the overall system.
Our Results
Our analysis establishes the necessary conditions for the adversary to undermine the system under various attack models. We also identify key system parameters that can be controlled by system operators in order to mitigate the impact of these attacks. Our results provide guidelines based on which system operators can take necessary measures to secure the dynamic pricing system.
More
|
|
Smart Grid Resilience Under Remote Meter Disconnect Attack
|
| Many smart meters on the market today include a service switch, allowing remote connection or disconnection (RCD) of electrical service over a utility’s communication network. While this feature is valuable for utilities, researchers have raised concerns about possible (ab)use by malicious attackers, noting the high economic cost of blackouts, as well the potential for controlled on-off switching of meters to affect power grid stability, for example by disturbing its frequency. However, while security concerns have been identified, little work has been done to develop and assess concrete countermeasures that are specific to these attacks.
|
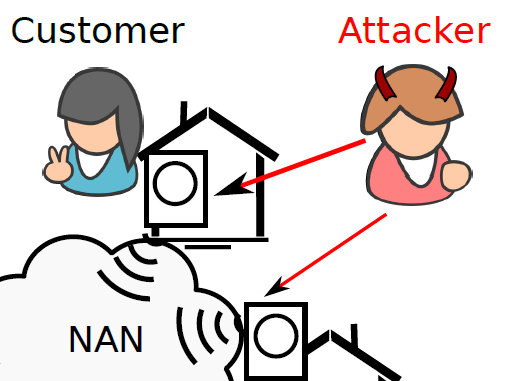 |
Our Approach
We focus on the modeling of a fundamental countermeasure — a random time delay at the meter for all RCD operations. Even if other countermeasures (e.g., authentication and key management) fail, this delay mechanism can provide the last line of defense by: 1) preventing rapid changes in overall system load; and 2) providing time for a utility to potentially detect and stop an attack in progress.
Our Results
Our analysis shows that even if an attacker successfully issues malicious RCD commands, a properly designed time delay mechanism of two hours or less can greatly reduce the magnitude of an RCD attack with little impact on a utility’s day-to-day operations. We also show that the nature of a utility’s non-security-related outages affect its resilience to RCD attacks.
More
|