Assessment Framework
| The complex nature of cyber-physical systems like the smart grid presents many security challenges. For example, subtle weaknesses in the underlying IT-infrastructure (as well as in computerized physical devices) can open entry points for malicious intruders and enable attacks with serious and far-reaching consequences (e.g., large-scale blackout). Our goal is to help stakeholders make use of the diverse information (network diagrams, device settings, known attacks, etc.) at their disposal to reason about the security of their system. | 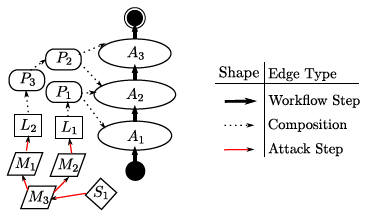 |
|
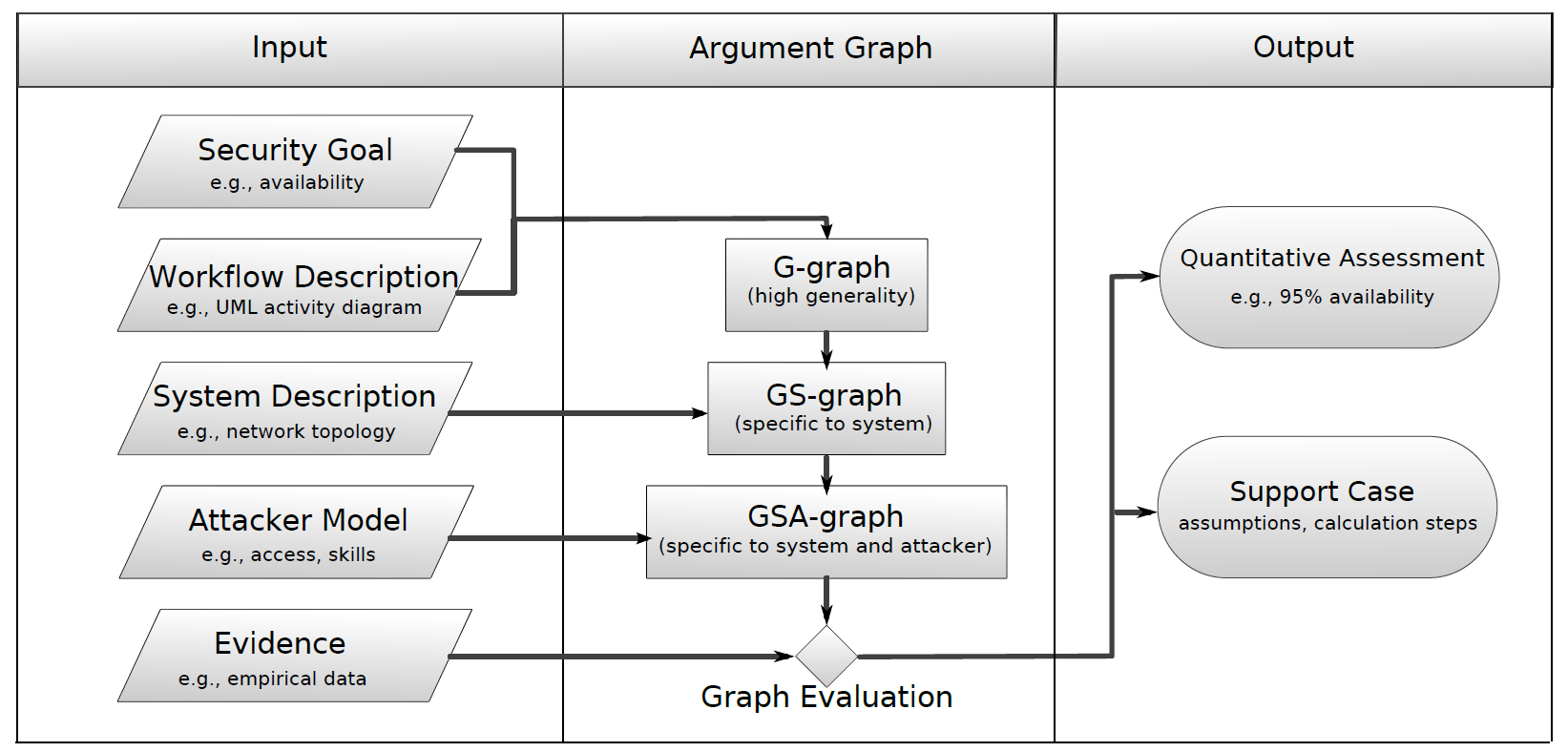
To achieve this, we introduce the concept of workflow–describing how a system provides its intended functionality–as a pillar of cybersecurity analysis. By focusing on the system’s functional workflows, our framework can integrate heterogeneous information about system components, empirical data, and attacker models to quantitatively reason about security goals in a largely automated fashion.
ChallengesA security assessment methodology should be rigorous, holistic, and scalable to large systems. Each of these objectives pose challenges (and tradeoffs) for researchers. Performance and reliability modeling frameworks may include rigorous mathematical underpinnings, but lack attacker models, and are difficult to apply for information properties like confidentiality. Conversely, many established attacker modeling frameworks from the security domain are not readily applicable to complex systems, since they lack workflow models to bridge the gap between IT infrastructure and other subsystems or actors. Most of the holistic approaches that exist today–e.g., assurance cases–are subjective in nature, and require a high level of human modeling effort. Such assessments may be constructed or interpreted differently by different security analysts, and do not scale well. |
||
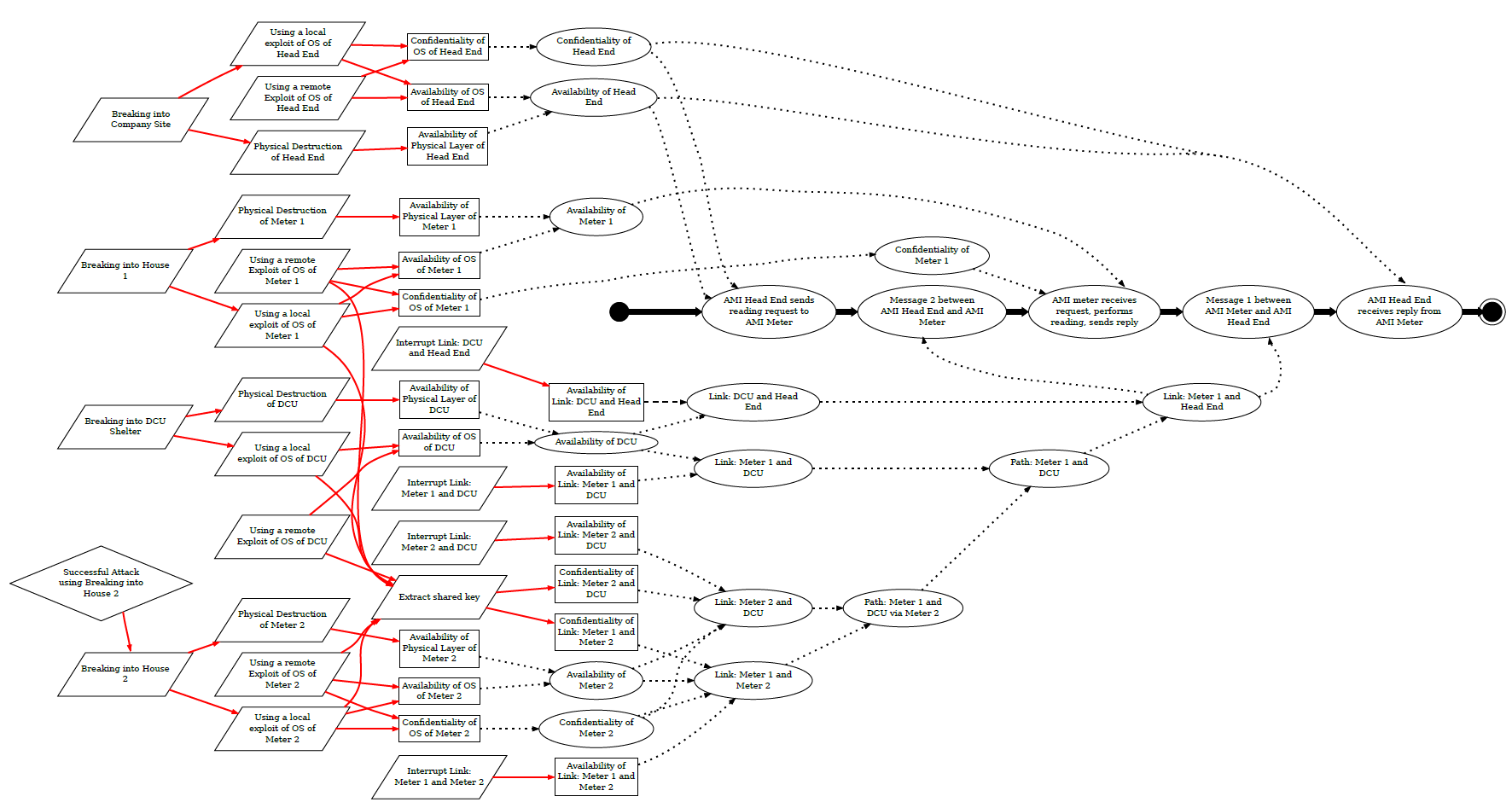
Our approachWe designed a framework that allows the integration of heterogeneous evidence for quantitative security assessments. In the core, this framework relies on workflows to model interactions in the system under consideration. A security assessment in this framework uses inputs from several distinct classes (security goal, workflow description, system description, attacker model, and evidence, as shown below) which are integrated in a systematic manner. By “going with the flow,” the assessment can naturally adopt a holistic view of the system, unifying information about system components, their properties, and possible attacks to argue about a security goal. This structure allows our approach to provide quantitative assessments in an automated fashion, while maintaining a broad assessment scope. Within this framework, we are investigating functions to combine and aggregate information during the evaluation of the central argument graph (example shown below). We have studied the use of Boolean algebra and Bayesian networks as possibilities. We are currently developing a software tool, CyberSAGE to automate this graph generation and quantitative assessment process. To compliment this work, we are also investigating several case studies from the smart grid domain. |
||
Publications
|
||