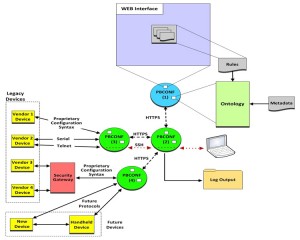
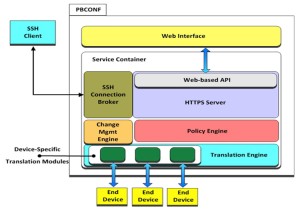
PBCONF System Overview
- Will leverage distributed architecture concepts to support both centralized and peer-based configuration of the devices to support scalability and resiliency.
- The system is a tree-like hierarchy. The master node can direct and control the nodes directly below it. It may directly configure end devices through remote access, direct subordinate instances, or it may do both.
- Communication is chained. Policy changes flow down the tree, security configuration changes propagate up the tree.
PBCONF Node
The system is composed of several functional components or subsystems that are contained within a PBCONF node. These nodes combine to provide the functionality of the PBCONF system. A node consists of a Web Interface and a Service Container. The Service Container is segmented into subcomponents, which include the:
- SSH connection broker,
- HTTPS server hosting Web-based API,
- Policy Engine,
- Change Management Engine, and a
- Translation Engine hosting the device-specific vendor modules.
Ontologies for Security Policies
One of the goals is the development of a well-specified and open ontology that represents the concepts and relationships of the security policy. The ontology will provide the basis for mapping the deploying organization’s security policy to the device-specific configurations. The policy rules will define constraints that a security configuration must meet. These can include user credentials, identity certificates and access control information.
Use Cases
Operations IT group would select the policy through the web interface. A compliance check is run by the system which will securely connect to each remote device, verify the current configuration and determine if it is in compliance with the selected policy.
- Secure change management: Each node maintains a Git repository that contains configuration information for all devices under its control. Any changes are compared and tracked by Git, and includes an audit log and time stamping.
- Monitoring for security configuration changes: Every node sends configuration changes of a device to its upstream node. The operating mode determines the scope of propagation. The device’s configuration is validated against the stored configuration before and after any changes. Any noncompliance is reported.
- Auditing and reporting: Alarm and notification system via emails and logging mechanism. Custom logging levels can be set.
- Secure remote access: Development of secure remote access protocols to a variety of transmission and distribution substation devices.
- Global policy application: Heartbeat communication among nodes to indicate status and policy revision.
- Authorization and non-repudiation: Will leverage X.509 identity certificates to validate communication between nodes. Identity verification required to access the API.