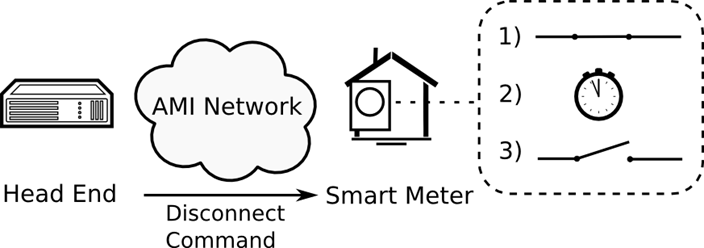
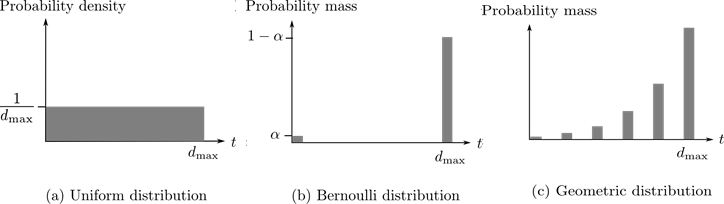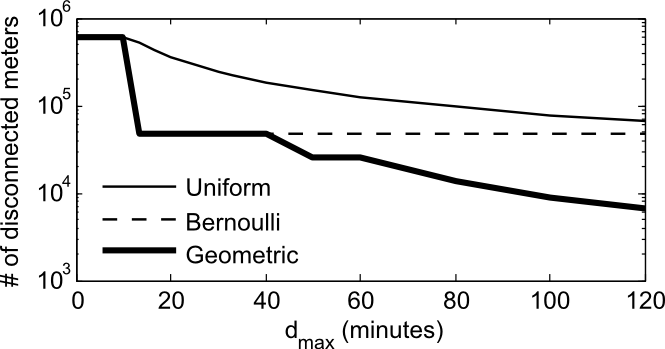Resilience to Smart Meter Disconnect Attacks
| Many smart meters on the market today include a service switch, allowing remote connection or disconnection (RCD) of electrical service over a utility’s communication network. While this feature is valuable for utilities, researchers have raised concerns about possible (ab)use by malicious attackers, noting the high economic cost of blackouts, as well the potential for controlled on-off switching of meters to affect power grid stability, for example by disturbing its frequency. However, while security concerns have been identified, little work has been done to develop and assess concrete countermeasures that are specific to these attacks. |  |
ChallengesUtility companies and vendors are introducing remote connect/disconnect capability because it provides tangible operational value: for example, switching off service to non-paying customers without dispatching a service technician. However, the feature also introduces security concerns. The primary challenge in this context is developing countermeasures to make the system more resilient against potential attacks, without undermining these practical operational use cases. Our approachWe focus on the modeling of a fundamental countermeasure — a random time delay at the meter for all RCD operations (shown in the figure below). Even if other countermeasures (e.g., authentication and key management) fail, this delay mechanism can provide the last line of defense by: 1) preventing rapid changes in overall system load; and 2) providing time for a utility to potentially detect and stop an attack in progress.
We develop three specific time delay countermeasures, using different probability density/mass functions as shown below. For each of these countermeasures, we evaluate the number of smart meters an adversary can compromise and shut off under the optimal attack strategy. Our resultsOur analysis shows that even if an attacker successfully issues malicious RCD commands, a properly designed time delay mechanism of two hours or less can greatly reduce the magnitude of an RCD attack with little impact on a utility’s day-to-day operations.
Our results also show that the nature of a utility’s non-security-related outages affect its resilience to RCD attacks by influencing its ability to differentiate normal outages from malicious events. Publications
|
|