Impact of Integrity Attacks on Real-Time Pricing in Smart Grids
1. Introduction
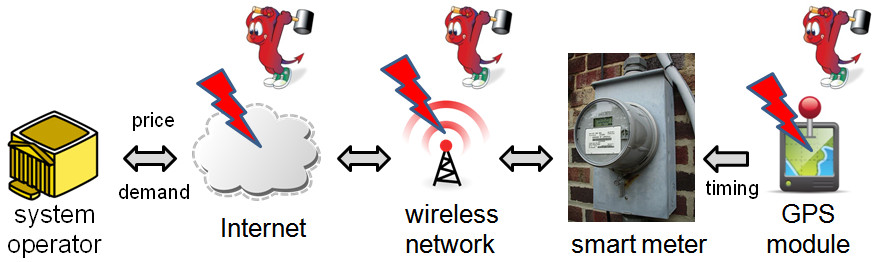
Fig. 1 Smart meters are exposed to various threats
Modern information and communication technologies used by smart grids are subject to cybersecurity threats. This work studies the impact of integrity attacks on real-time pricing (RTP), a key feature of smart grids that uses such technologies to improve system efficiency. Recent studies [1] have shown that RTP creates a closed loop formed by the mutually dependent real-time price signals and price-taking demand. Such a closed loop can be exploited by an adversary whose objective is to destabilize the pricing system. Specifically, small malicious modifications to the price signals can be iteratively amplified by the closed loop, causing inefficiency and even severe failures such as blackouts. This work adopts a control-theoretic approach to deriving the fundamental conditions of RTP stability under two broad classes of integrity attacks, namely, the scaling and delay attacks. We show that the RTP system is at risk of being destabilized only if the adversary can compromise the price signals advertised to smart meters by reducing their values in the scaling attack, or by providing old prices to over half of all consumers in the delay attack. The results provide useful guidelines for system operators to analyze the impact of various attack parameters on system stability, so that they may take adequate measures to secure RTP systems.
1.1 Market Model, RTP Problem, and Solution Stability
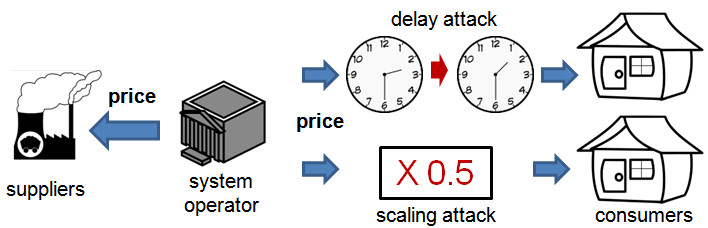
As shown in Fig. 2, the electricity market considered in this work consists of an independent system operator (ISO), a set of consumers, and a set of suppliers. The ISO is a profit-neutral agent which aims to clear the market, i.e., match supply and demand. It determines a clearing price every 0.5 or 1 hours and announces it to the suppliers and end consumers. Upon receiving the real-time price for the next pricing period, consumers and suppliers will make decisions on how much they will consume and supply in the next period. The analysis in this work assumes general abstract demand and supply models for the consumers and suppliers. Concrete empirical demand and supply models commonly used in literature include the constant elasticity of own-price demand model and the linear supply model, which are used to drive the numerical experiments and simulations in this work.
At the beginning of each pricing period, the ISO aims to find the clearing price such that the scheduled supply matches demand. However, the ISO usually has limited knowledge about the consumers. In practice, the ISO first predicts the demand, and sets the price to match the scheduled supply and predicted demand. Straightforward solutions to this problem may lead to significantly fluctuating prices, due to the unstable closed loop formed by the feedback from the demand prediction according to historical demand. For instance, in this work, we extensively examine the stability of an autoregression-based direct feedback approach studied in [1]. The results show that it can be unstable with significant probabilities under the two empirical demand and supply models. The price oscillation of an unstable RTP system may lead to severe consequences. For example, when the diverging prices reach low values, the increased demand may cause overload of the transmission and distribution networks.
Fig. 2 The market and attack models
The empirical study on the direct feedback approach shows the necessity of well-designed control laws for stabilizing the RTP systems. Based on the classical discrete-time control theory, we develop a basic price stabilization algorithm with provable stability. The security of this algorithm provides fundamental baselines for understanding the security properties of RTP systems based on more sophisticated price stabilization algorithm that could be developed. Specifically, our algorithm sets the price adjustment proportional to the error between the demand and supply in the last pricing period. Extensive simulations show that this basic algorithm successfully matches supply and demand under a wide range of settings, and remains stable in the presence of various dynamics.
1.2 Attacks and Their Impacts
This work focuses on the integrity attacks that maliciously change the price signals. We consider integrity attacks on the price signals received by a subset of consumers. In smart grids, the real-time price signals are exposed to different security threats at the source, during network transmissions, and at the consumer-level smart meters. Recent reverse engineering and penetration tests [2, 3] have shown that many smart meters lack basic security measures to ensure integrity and authenticity of the input/output data. These security vulnerabilities can be exploited to maliciously change the price signals. In particular, we consider the following two kinds of integrity attacks:
- Scaling attack: The compromised price is a scaled version of the true price;
- Delay attack: The compromised price is an old price.
Compared with the attacks that can arbitrarily modify the price signals, the above two “constrained” attacks can be realized with lower capability and resource requirements. For instance, the delay attack can be launched by modifying the smart meters’ internal clocks. Smart meters typically assign a memory buffer to store received prices. If a smart meter’s clock has a lag, it will store newly received prices in the buffer and apply an old price for the present. Furthermore, attacks on the clocks can be realized by compromising the vulnerable time synchronization services in smart grids [4].
In this work, we use a control-theoretic metric, region of stability (ROS), to characterize the impacts of attacks. The ROS is the region for the system and attack parameters, in which the RTP system is stable. We apply extensive control-theoretic analysis to derive the ROS under the two attacks. In particular, we show that the RTP system is at risk of being destabilized only if the adversary can compromise the price signals advertised to smart meters by reducing their values in the scaling attack, or by providing old prices to over half of all consumers in the delay attack.
1.3 Trace-Driven Simulations
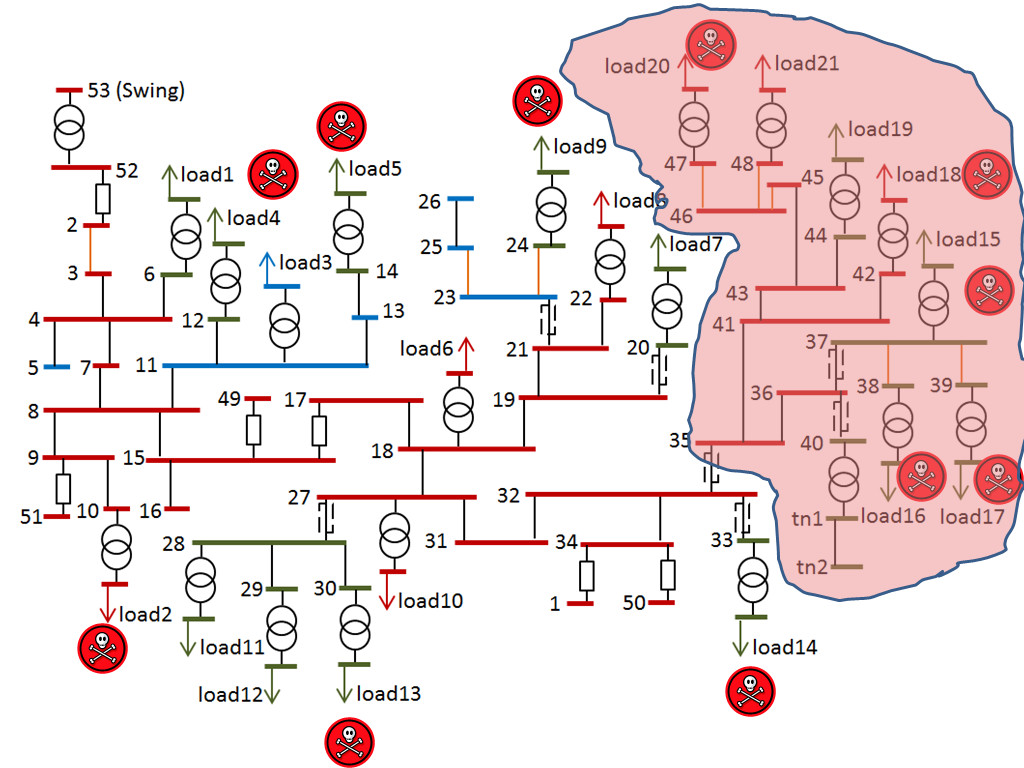
We use GridLAB-D, an electric power distribution system simulator, to evaluate the impact of integrity attacks. GridLAB-D captures many physical characteristics such as power line capacities and impedances. It can record emergency events that occur when the current ratings of lines and power ratings of transformers are exceeded. Such events could cause sustained service interruptions to consumers. We use a distribution feeder specification that comprises 1405 houses, which is illustrated in Fig. 3. To improve the realism of the simulations, we use the half-hourly total demand trace from March 1st to 22nd, 2013, of New South Wales, Australia, provided by AEMO as the load of consumers.
Fig. 3 An illustration of the simulated distribution feeder. (The skulls represent compromised loads and the shaded area represents the blackout region.)
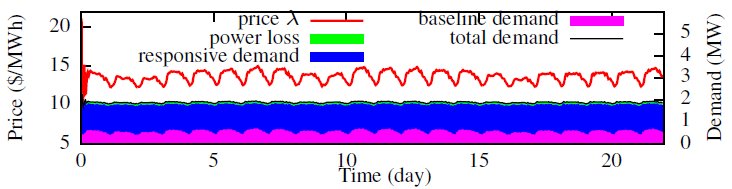
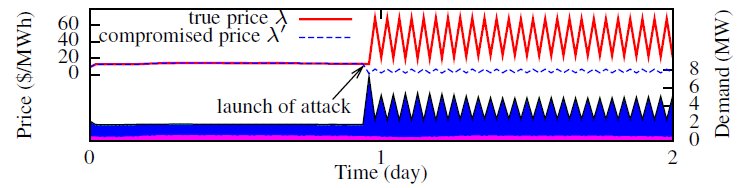
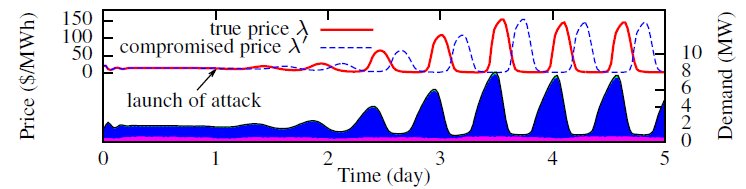
Fig. 4 shows the price and resultant demands under our price stabilization algorithm. The price well adapts to the time-varying load. The error between supply and demand is close to zero, which means that the clearing price is achieved. Fig. 5 plots the true and compromised prices, as well as the breakdown of demand under the scaling attack. We can see that the price and the demand fluctuates severely. Fig. 6 shows the results under the delay attack. A small error between demand and supply is amplified iteratively along the control loops, after the launch of the attack.
Fig. 4 Price stabilization in the absence of attacks
Fig. 5 Scaling attack (all consumers are compromised, price is scaled down by 10 times)
Fig. 6 Delay attack (all consumers are compromised, price is delayed for 4.5 hours)
2. People
 Rui Tan Rui TanResearch Scientist at ADSC tanrui@adsc.com.sg |
 Varun Badrinath Krishna Varun Badrinath KrishnaSoftware Engineer at ADSC Varun.BK@adsc.com.sg |
 David K. Y. Yau David K. Y. YauSmart Grid Program Director and Distinguished Scientist at ADSC Professor at Singapore University of Technology and Design david.yau@adsc.com.sg |
 Zbigniew Kalbarczyk Zbigniew KalbarczykResearch Professor at University of Illinos at Urbana-Champaign kalbarcz@illinois.edu |
3. Publication
- Rui Tan, Varun Badrinath Krishna, David K.Y. Yau, and Zbigniew Kalbarczyk. 2013. Impact of integrity attacks on real-time pricing in smart grids. In Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security (CCS ’13). ACM, New York, NY, USA, 439-450. [PDF]
4. Acknowledgements
This work was supported in part by Singapore’s Agency for Science, Technology and Research (A*STAR) under the Human Sixth Sense Programme, and in part by U.S. National Science Foundation under grant numbers CNS-0963715 and CNS-0964086.
5. References
[1] M. Roozbehani, M. Dahleh, S. Mitter. Volatility of Power Grids under Real-Time Pricing. IEEE Transactions on Power Systems, 27(4): 1926-1940, 2012
[2] S. McLaughlin, D. Podkuiko, S. Miadzvezhanka, A. Delozier, P. McDaniel. Multi-Vendor Penetration Testing in the Advanced Metering Infrastructure. In Annual Computer Security Applications Conference (ACSAC), 2010.
[3] I. Rouf, H. Mustafa, M. Xu, W. Xu, R. Miller, M. Gruteser. Neighborhood Watch: Security and Privacy Analysis of Automatic Meter Reading Systems. In ACM Conference on Computer and Communications Security (CCS), 2012.
[4] T. Nighswander, B. Ledvina, J. Diamond, R. Brumley, D. Brumley. GPS Software Attacks. In ACM Conference on Computer and Communications Security (CCS), 2012.