Cyber-Physical System and Critical Infrastructure Security
Overview
|
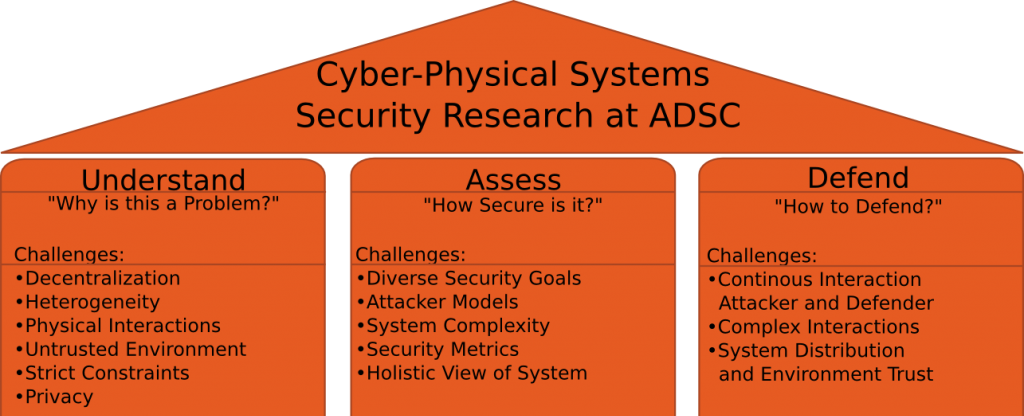
In recent years, Cyber-Physical Systems (CPS) have emerged from traditional engineered systems in the areas of power and energy, transportation, healthcare, and manufacturing. By introducing pervasive communication support in those systems, they have become more flexible, performant, and responsive. In general, these CPS are also mission-critical: their availability and correct operation is essential. At ADSC, research in the security of Cyber-Physical Systems started with our work on Smart Grid Security in 2011. From 2014-2017 this research expanded to cover other systems and technologies that underpin smart cities, such as urban transportation systems and the internet of things. In 2017, ADSC relocated to the Campus for Research Excellence and Technological Enterprise (CREATE) and began a 5-year program focused on ensuring the cybersecurity and trustworthiness of the electric power grid.
|
Synergy and Collaborations
ADSC actively collaborates with peer research institutes, industry partners, and universities in Singapore, including:
- Singapore University of Technology and Design (SUTD)
- Agency for Science, Technology, and Research (A*STAR)
- National University of Singapore (NUS)
- Nanyang Technological University (NTU)